The Governor's budget proposes $14 million total funds across various departments to strengthen information security. In this analysis, we discuss our findings and recommendations regarding the state's approach towards strengthening information security.
February 28, 2017
The 2017-18 Budget
Governor’s Proposal to Strengthen Information Security
The Governor’s budget proposes $14 million total funds across various departments to strengthen information security. In this analysis, we discuss our findings and recommendations regarding the state’s approach towards strengthening information security.
Background
Role of Department of Technology. The California Department of Technology (CDT), a department within the California Government Operations Agency, is the state’s central information technology (IT) organization and has broad authority over all aspects of technology in state government. It was created to provide technology-related expertise to the state, and its purview generally extends to departments that are under the direct authority of the Governor (therefore excluding, for example, constitutional offices).
What Is Information Security? Information security refers to the protection of physical and electronic data, and IT systems, hardware, and software, from a wide spectrum of threats and risks. Implementing appropriate security measures is critical to ensure continuity of state operations and protect information against unauthorized access, use, disclosure, disruption, modification, or destruction. In the past several years, retailers, financial institutions, and governments have increasingly fallen victim to information security attacks. Given the extensive assortment of sensitive data that the state maintains, including Social Security numbers, health records, and income tax information, the state is a prime target for information security attacks. Not only can information security breaches impede the state’s ability to serve the public, but the costs both to the state and to the individuals affected could be substantial. We note that information maintained within the state’s various IT systems has different levels of sensitivity and requires different levels of protection. Based upon the sensitivities of the data maintained in IT systems, the controls that are in place to protect that data vary.
Who Is Responsible for the State’s Information Security? In August 2015, the Governor issued an executive order to establish the California Cybersecurity Information Center (Cal-CSIC) as a coordinating entity for departments involved in protecting the state’s computer networks and IT infrastructure. Cal-CSIC is a partnership between CDT, California Office of Emergency Services, California Military Department, and California Highway Patrol. Each department contributes its own expertise towards fulfilling the Cal-CSIC’s mission to reduce the likelihood and severity of information security incidents in the state. CDT, in particular, has an oversight role that calls on it to (1) set information security policies, standards, and procedures and (2) ensure that departments maintain the confidentiality, integrity, and availability of their IT systems and protect the privacy of the state's information. Please refer to the nearby box for a description of the other partners’ contributions to information security.
Responsibilities of Information Security Partners
The California Department of Technology, California Office of Emergency Services (OES), California Military Department (CMD), and California Highway Patrol (CHP) work in partnership to reduce the likelihood and severity of information security incidents in the state. Each department contributes its own expertise towards addressing the state’s information security needs. OES coordinates the state’s efforts related to information security by gathering intelligence and sharing information related to security threats. CMD provides services to departments, such as assessments of security vulnerabilities and training, to assist them in meeting the state’s information security requirements. Finally, CHP collects information about computer crime incidents and investigates those incidents.
Recent Changes to CDT’s Information Security Practices. In August 2015, the California State Auditor found that many state departments had poor security controls over their IT systems and that CDT had failed to provide effective oversight of departments’ information security. The auditor found that these security deficiencies could compromise the IT systems that departments use to perform their daily operations. Since then, CDT has made several changes to strengthen its oversight of information security. Specifically, it:
Prioritized and Simplified State Security Standards. According to the State Auditor, more than half of the departments it evaluated indicated that CDT's guidance for complying with security standards was insufficient. CDT has since prioritized and simplified some of the standards that departments are required to comply with in order to focus on the most important and relevant standards and to make them more easily understood by departments.
Required Routine Security Assessments. Recently, CDT has required routine independent security assessments of departments under its purview to determine their vulnerabilities—weaknesses in information system security procedures or the identification of components of IT systems that could be exploited by a threat. This is consistent with legislation passed in 2015 requiring no fewer than 35 assessments be completed each year. (While CDT has long required departments to perform security assessments every two years to determine their vulnerabilities, these assessments have not been performed consistently.)
Established Security Compliance Audits. CDT has long required departments to annually self-certify that they are complying with the state’s information security policies, standards, and procedures. The State Auditor found deficiencies with CDT’s information security oversight because it did not verify departments’ self-certifications. Some departments either did not self-certify or certified without actually being compliant. In response to these findings, in 2016 CDT established an information security compliance audit program that verifies whether departments are meeting the standards that they have self-certified and that they have addressed any previously identified security vulnerabilities (such as those identified through previous security assessments). (The audit program was previously piloted before it was officially established in 2016.) Given limited resources, CDT targets its audits to a select group of departments.
Conducted One-Time Security “Maturity” Assessment. In 2016, CDT contracted with a vendor to conduct a one-time analysis of the security maturity of 20 departments. Maturity is an indicator of how prepared departments are to prevent or respond to a security attack in a way that mitigates any negative consequences. Low maturity departments are not well prepared for attack and generally react to security incidents rather than proactively working to prevent them from occurring. In contrast, high maturity departments have an established culture of proactive security monitoring. The purpose of the assessment was to obtain a snapshot of the maturity of the departments analyzed and inform the state’s efforts to strengthen information security. The assessment also served to validate the self-certifications of participating departments. The assessment found the state generally performed below the minimum maturity target across departments.
Establishing Statewide Inventory of Information Assets and Their Maturity. CDT is also implementing the California Compliance and Security Incident Reporting System (Cal-CSIRS) to capture information from departments’ self-certifications, security breach incidents, and system outages lasting two or more hours. When this system is fully implemented by the end of 2017, it will create a statewide inventory of information assets—any state-owned data, systems, hardware, or software—and their maturity. CDT will use the inventory to better manage its oversight of information security.
Governor’s 2017-18 Budget Proposals
Governor’s Budget Proposes $14 Million Across Various Departments to Strengthen Information Security. The Governor’s 2017-18 budget includes $13.9 million ($4 million General Fund) and 58 positions across 12 departments to strengthen the state’s information security operations. The proposals include various approaches to strengthening information security based on the specific vulnerabilities the departments identified. Some departments would establish continuously operating security centers to monitor threats, others would develop mitigation plans to reduce the risk of threats, while still others would establish department policies and procedures to achieve security compliance and train staff on information security procedures. Figure 1 provides a listing of the information security budget proposals.
Figure 1
Governor’s 2017-18 Budget: Information Security Proposals
(Dollars in Millions)
|
Department |
Proposed Expenditures |
Positions |
|
|
Total Funds |
General Fund |
||
|
Department of Transportation |
$4.0 |
— |
6 |
|
Department of Corrections and Rehabilitation |
2.6 |
$2.6 |
8 |
|
California Highway Patrol |
1.8 |
— |
14 |
|
Department of Technology |
1.2 |
— |
9 |
|
State Controller’s Office |
1.0 |
0.5 |
2 |
|
Public Utilities Commission |
0.7 |
— |
4 |
|
Department of Managed Health Care |
0.7 |
— |
2 |
|
State Teachers’ Retirement System |
0.6 |
— |
5 |
|
Department of Developmental Services |
0.4 |
0.3 |
3 |
|
Department of Rehabilitation |
0.3 |
0.3 |
2 |
|
Department of Alcoholic Beverage Control |
0.3 |
— |
2 |
|
State Treasurer’s Office |
0.3 |
0.3 |
1 |
|
Totals |
$13.9 |
$4.0 |
58 |
LAO Assessment
Budget Proposals Seem Reasonable on an Individual Department Level . . . Based on our review, we do not raise any particular concerns with each of the 12 budget proposals across various departments to strengthen information security. We understand it is CDT’s practice to review IT-related budget proposals, including these security-related proposals. Although CDT did not initiate these proposals, it indicates that as part of its review, it validated the security issue identified by the department proposing its own proposal and assessed whether the department was taking a reasonable approach towards addressing the issue. This review is valuable given that CDT was created to provide IT-related expertise and the individual departments may not always know the best practices for addressing a security vulnerability that they face.
. . . But Unclear Whether Proposals Address the State’s Most Critical Security Risks. Although we are not raising any particular concerns with the individual proposals, we are concerned that because they were generally initiated by the individual departments, it is unclear whether they collectively address the state’s most critical security risks—the IT systems with the most significant vulnerabilities and the most sensitive information. The individual departments do not have a comprehensive view of the entire state’s security needs and therefore whether their individual information security needs are the most critical to address across state government. While CDT reviewed these individual requests to verify that there was some level of information security need, it did not determine whether the requested resources addressed the state’s most critical information security issues. For example, a department may have high vulnerability but the associated information that would be released in the event of a security breach is not particularly sensitive. Consequently, this may not be the most critical vulnerability to resolve when other departments may have vulnerabilities that may lead to catastrophic consequences should information be breached or confidentiality not protected. Additionally, it is possible that departments that did not come forward with a budget request might have more critical security risks but are unaware of their own vulnerabilities. Figure 2 depicts this security vulnerability and sensitivity matrix. Ideally, the Legislature would want to make sure the state is focusing its attention and resources on addressing the IT systems that present the most critical security risks—those in the upper right quadrant of the figure.
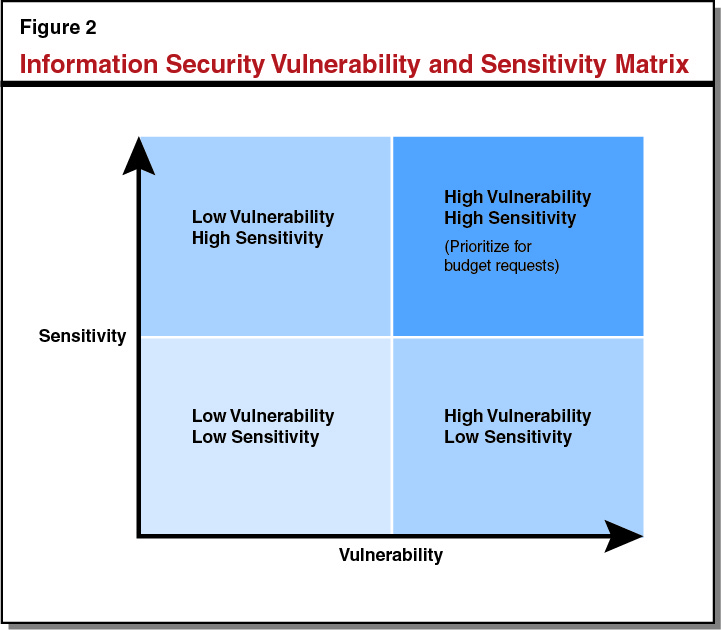
Recent Efforts by CDT Move in the Right Direction, but Were Not in Place to Inform Budget Proposals. In recent years, and in response to the recent audit by the State Auditor, CDT has made several changes to its practices in order to strengthen its information security controls. As mentioned earlier, CDT has required security assessments that identify vulnerabilities and establish a roadmap for addressing the vulnerabilities, and established a security compliance audit program. Additionally, the new state inventory—Cal-CSIRS—could help identify the state’s security vulnerabilities. However, the new processes established by CDT stop short of assessing the sensitivity of the information contained in the system. Additionally, while these changes are moves in the right direction, they were not in place in time to inform the information security-related budget proposals before the Legislature. This lack of a strategic approach makes it unclear whether the proposals address the state’s most critical information security issues.
LAO Recommendations
CDT Should Take Leadership Role Ensuring Future Proposals Address Critical Security Risks. We believe that, going forward, CDT should take a strategic leadership role in identifying, prioritizing, and addressing the state’s information security vulnerabilities using best practices. The steps CDT has recently taken go a long way in fulfilling this role and helping the state make strategic investments in information security. We recommend the Legislature direct CDT to use the analysis from the new processes to inform future requests for budget augmentations to strengthen information security. As a next step, we recommend that the Legislature direct CDT to consider the impact associated with a security breach and direct the administration to prioritize addressing high-vulnerability and high-sensitivity security risks for future budget requests. (We note that departments outside CDT’s jurisdiction would generally not be reflected in this strategic approach. Requests from these departments would generally not benefit from CDT’s strategic leadership and would have to be evaluated by the Legislature on a case-by-case basis.) Our recommendations address the current absence of a strategic approach on information security that makes it difficult for the Legislature to determine if these proposals address the most critical issues.
Direct Administration to Report at Budget Hearings on Whether Current Proposals Address Reasonable Security Risks. Although we are not raising any particular concerns with the individual proposals, it is not clear that they address the areas where the state (1) is the most vulnerable and (2) has the most sensitive data. This is because the proposals did not benefit from CDT’s new efforts to better assess IT security vulnerabilities. It is unlikely that CDT will be able to accomplish the type of comprehensive assessment we are recommending in time for the 2017-18 proposals. Instead, we recommend the Legislature use budget hearings to request that the departments make a convincing case to the Legislature that their proposals address reasonable IT security vulnerabilities that involve sensitive data.
